Experience next-level digital storage with NFC Vault — where your data stays safe, accessible, and lightning-fast.
Learn More →
In the era of remote work, securing sensitive data against unauthorized access has never been more critical. Businesses face the daunting challenge of ensuring that their security measures are robust enough to protect against the sophisticated tactics employed by cyber attackers. Multi-Factor Authentication (MFA) stands as a crucial defense mechanism, yet its implementation is not without hurdles.
The shift to remote work has expanded the attack surface, increasing the vulnerability to data breaches and unauthorized access.
Businesses often grapple with the complexity of integrating MFA across diverse systems and platforms.
There's a tangible resistance from users adapting to additional security steps, perceived as hurdles to productivity.
Ensuring MFA solutions are compatible with existing security systems poses a significant challenge for IT departments.
Drive mapping is an important feature for online file access. End users can easily drag and drop files and folders from a set of mapped drives over the Internet without a VPN connection.
File locking is a vital feature for online file access and team collaboration to avoid conflicts. End users need to control global concurrent online file access by using file locking to maintain consistency.
Have you spent many hours troubleshooting VPN connections? Have both your staff and IT support team lost productivity due to downed VPN connections? VPNs are complicated; there is a better way!
To counteract evolving cyber threats, Multi-Factor Authentication (MFA) serves as an effective safeguard, bolstering security while maintaining user convenience. MFA enhances protection by necessitating extra verification steps, significantly diminishing the likelihood of unauthorized access and safeguarding sensitive information in any remote work scenario.
MFA adds a critical layer of security, requiring a second form of verification that drastically lowers the chances of unauthorized data access.
Easily integrates with existing systems and platforms, ensuring a smooth transition and deployment across diverse IT environments.
Designed with the end-user in mind, MFA offers a straightforward authentication process that does not hinder productivity.
Supports a wide range of authenticators, from mobile apps to hardware tokens, offering flexibility in how users secure their accounts.

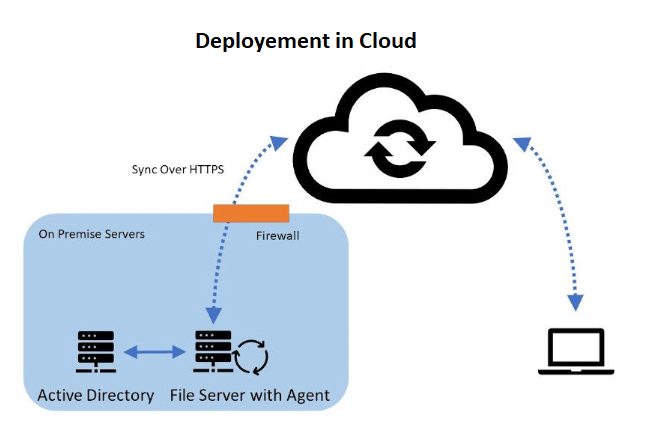
Gladinet enables seamless file server integration with support for Windows 2016/2019/2022, offering indirect & direct connection options and flexible access.
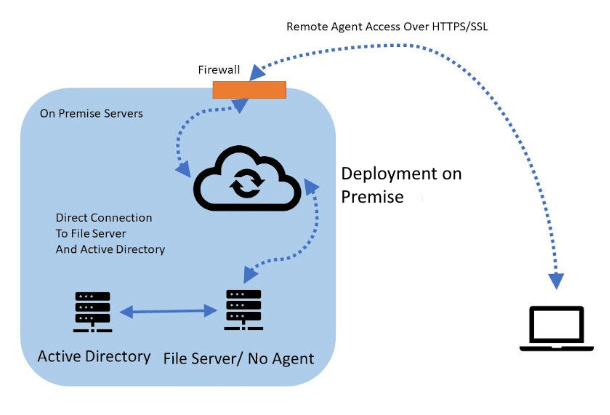
Gladinet provides a direct file access solution from remote devices and mobile devices, offering a streamlined and secure method to access internal file servers via HTTPS/SSL.
Multi-Factor Authentication (MFA) bolsters your business’s security by necessitating multiple verification forms for access, crucial for protecting sensitive data, particularly in remote work settings. Our MFA solution integrates with NFC Vault and CentreStack, providing a comprehensive defense against unauthorized entry, and is a vital part of your security strategy.
When a user attempts to log in, the system prompts for the usual username and password, initiating the MFA process.
After entering the primary credentials, the user is asked for a second form of verification, which could be a code sent to their mobile device or an authentication app.
The user must provide this second verification factor, further proving their identity and securing the login process.
Once both verification steps are successfully completed, access to the sensitive data or system is granted, ensuring secure, authenticated access.
Our MFA solution integrates with various authenticators and supports compatibility across different devices, enhancing security without sacrificing convenience.

A leading eLearning provider revolutionized its document sharing capabilities through a strategic partnership, achieving unparalleled security and user accessibility in the cloud. This transformation addressed critical challenges, including inadequate security features and operational inefficiencies, by implementing a solution that integrated seamlessly with AWS S3 buckets. Enhanced security measures, a user-friendly interface, and operational compatibility led to robust data protection, improved customer experience, and operational excellence. This case underscores the importance of tailored technological solutions in elevating business operations and customer satisfaction in the eLearning sector.

A leading real estate company transformed its operations by adopting CentreStack, a flexible and secure data management solution. This strategic move addressed their challenges of outdated systems and remote access limitations, resulting in enhanced operational efficiency, significant cost savings, and robust security measures. The transition to CentreStack not only streamlined data migration and access across devices but also supported the company’s growth trajectory. This case study exemplifies the power of tailored solutions in revolutionizing industry-specific operations and achieving remarkable business outcomes.